Surf shark One is one of the fast VPN solution compatible with desktop devices, notebooks, smartphones, tablets,...
CYBERSECURITY
Welcome to our Cybersecurity category, your trusted guide to staying safe in the digital world. Whether you’re learning about data protection, threat prevention, or online privacy, this space delivers clear insights and practical advice. Explore expert tips, real-world strategies, and the latest trends shaping cyber defence. Dive in to stay informed, strengthen your security awareness, and protect what matters most in the connected age.
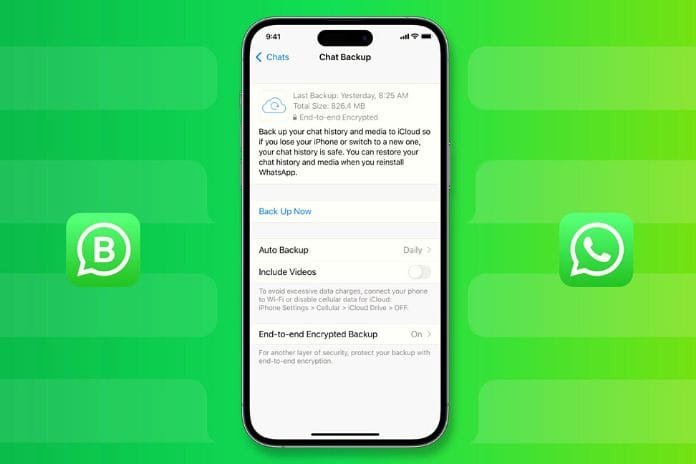
Applications such as WhatsApp often store information that would be very sad to lose. In that case,...
Differences between setting up a VPN manually and installing a paid VPN service. What changes and what...
Securing company buildings with locks and alarm systems is a matter of course but what about data...
Print workflows and IT infrastructure are key considerations when choosing between VPN and cloud printing to meet...
We are facing global digital addiction, rapidly transforming how things work, further accentuating the pandemic and its...
Organizations increasingly rely on the cloud to store mission-critical information in virtually every aspect of their business—from...
From the network to our daily life, security is an essential element of the digital transformation we...
Your smartphone effectively becomes a key to accessing secured areas thanks to mobile access control. Mobile access...
Security Monitoring: To be effective, SOCs need to be constantly evolving. What does the future hold for...